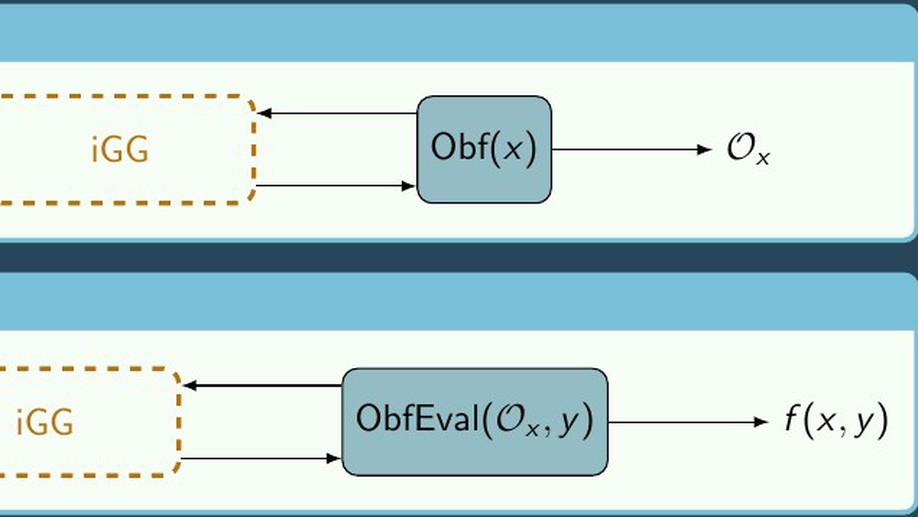
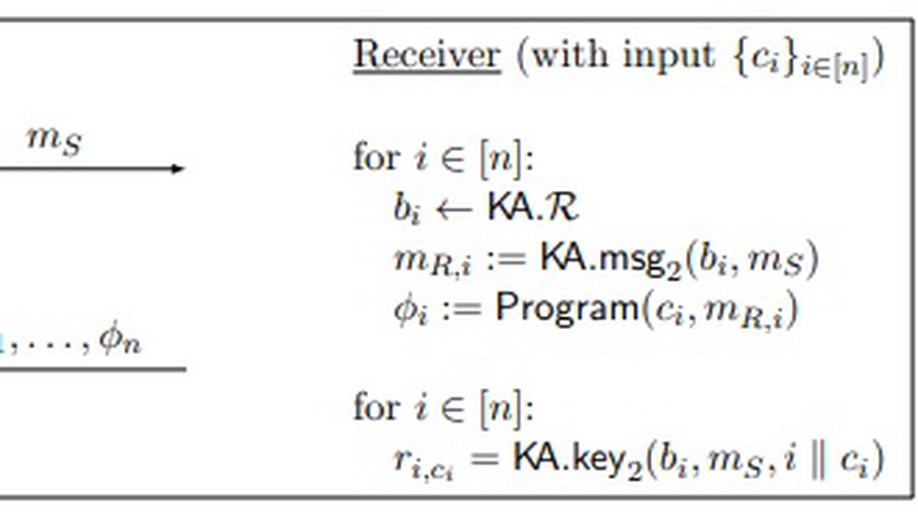
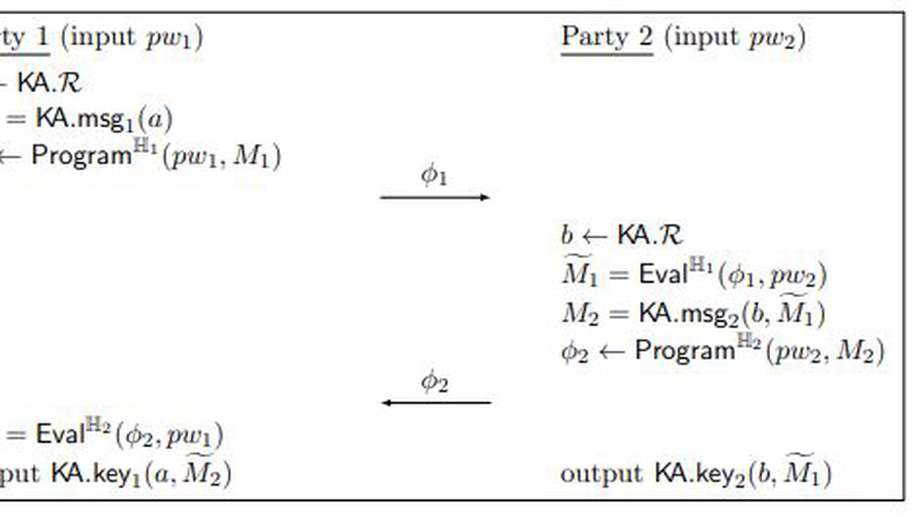
We introduce an analogous idea to strong asymmetric security (Jarecki, Krawczyk, Xu 2019) for secure two-party computation which we refer to as input obfuscated two party computation (io2PC). In io2PC, compromising the server’s long-term storage doesn’t immediate leak their input, but rather an oracle to a residual function. This means that the adversary must perform an amount of computation (observable to the simulator) to find the server’s underlying input proportional to an online attack. In doing so, we provide a compiler from virtual black box obfuscations in the random oracle model and generic group model to io2PC protocol realizing the same functions. To achieve this, we construct a generic group analog to an oblivious psuedorandom function where the server mediates interaction with a generic group family indexed by the server’s private input.